LUKS Encrypted Disks under Ubuntu 10.10

This posting is mostly just a reference for myself since I don’t do this often enough for me to have it memorized. These are the steps I use to create LUKS encrypted disks to use as a backup target that I can take off-site. Since they’re off site and stored in my desk where others may have access to the disks, I want to make sure that I’m the only one with access to the data. I use bare OEM style hard drives in a Thermaltake BlacX hard drive docking station. I have one at home and one at the office.
Before I store a backup on a disk, it needs to be set it up for LUKS encryption. This posting explains that part of the process.
WARNING: Following these steps will erase disks and lose data!
Consider yourself duly warned. I also do everything from the command line except the final steps. There are GUI tools to do this as well, but the command line is much quicker for me.
To start, I load a drive into the dock and power it up. In this case, the drive I’m loading is a 500G Maxtor drive.
From a shell window, I issue the ‘dmesg’ command to determine which drive it came up as:
marc@fozzie:~$ dmesg
[535060.118638] usb 1-1.4.4: new high speed USB device using ehci_hcd and address 9
[535060.230194] usb-storage 1-1.4.4:1.0: Quirks match for vid 152d pid 2329: 8020
[535060.230358] scsi13 : usb-storage 1-1.4.4:1.0
[535061.228868] scsi 13:0:0:0: Direct-Access MAXTOR S TM3500630AS PQ: 0 ANSI: 2 CCS
[535061.229582] sd 13:0:0:0: Attached scsi generic sg8 type 0
[535061.230173] sd 13:0:0:0: [sdi] 976773168 512-byte logical blocks: (500 GB/465 GiB)
[535061.230918] sd 13:0:0:0: [sdi] Write Protect is off
[535061.230922] sd 13:0:0:0: [sdi] Mode Sense: 34 00 00 00
[535061.230925] sd 13:0:0:0: [sdi] Assuming drive cache: write through
[535061.232459] sd 13:0:0:0: [sdi] Assuming drive cache: write through
[535061.232464] sdi: sdi1
[535061.249699] sd 13:0:0:0: [sdi] Assuming drive cache: write through
[535061.249703] sd 13:0:0:0: [sdi] Attached SCSI disk
So it came up as /dev/sdi. This particular disk I was once using with Fedora before I switched over to using Ubuntu, so I know there are partitions on it. I’ll need to get rid of those first using fdisk, and then create a single new partition on it:
marc@fozzie:~$ sudo fdisk /dev/sdi
WARNING: DOS-compatible mode is deprecated. It's strongly recommended to
switch off the mode (command 'c') and change display units to
sectors (command 'u').
Command (m for help): p
Disk /dev/sdi: 500.1 GB, 500107862016 bytes
255 heads, 63 sectors/track, 60801 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk identifier: 0x33dc2272
Device Boot Start End Blocks Id System
/dev/sdi1 * 1 60802 488386583+ 8e Linux LVM
Command (m for help): d
Selected partition 1
Command (m for help): n
Command action
e extended
p primary partition (1-4)
p
Partition number (1-4): 1
First cylinder (1-60801, default 1):
Using default value 1
Last cylinder, +cylinders or +size{K,M,G} (1-60801, default 60801):
Using default value 60801
Command (m for help): w
The partition table has been altered!
Calling ioctl() to re-read partition table.
Syncing disks.
So now the disk is ready. Set up the encryption.
marc@fozzie:~$ sudo cryptsetup --verify-passphrase luksFormat /dev/sdi1 -c aes -s 256 -h sha256
WARNING!
========
This will overwrite data on /dev/sdi1 irrevocably.
Are you sure? (Type uppercase yes): YES
Enter LUKS passphrase:
Verify passphrase:
marc@fozzie:~$ sudo cryptsetup luksOpen /dev/sdi1 backups01
Enter passphrase for /dev/sdi1:
marc@fozzie:~$ sudo fdisk /dev/mapper/backups01
Device contains neither a valid DOS partition table, nor Sun, SGI or OSF disklabel
Building a new DOS disklabel with disk identifier 0x75dd258c.
Changes will remain in memory only, until you decide to write them.
After that, of course, the previous content won't be recoverable.
Warning: invalid flag 0x0000 of partition table 4 will be corrected by w(rite)
WARNING: DOS-compatible mode is deprecated. It's strongly recommended to
switch off the mode (command 'c') and change display units to
sectors (command 'u').
Command (m for help): n
Command action
e extended
p primary partition (1-4)
p
Partition number (1-4): 1
First cylinder (1-60800, default 1):
Using default value 1
Last cylinder, +cylinders or +size{K,M,G} (1-60800, default 60800):
Using default value 60800
Command (m for help): w
The partition table has been altered!
Calling ioctl() to re-read partition table.
WARNING: Re-reading the partition table failed with error 22: Invalid argument.
The kernel still uses the old table. The new table will be used at
the next reboot or after you run partprobe(8) or kpartx(8)
Syncing disks.
marc@fozzie:~$ sudo mkfs.ext4 -Lbackups01 /dev/mapper/backups01
mke2fs 1.41.12 (17-May-2010)
Filesystem label=backups01
OS type: Linux
Block size=4096 (log=2)
Fragment size=4096 (log=2)
Stride=0 blocks, Stripe width=0 blocks
30531584 inodes, 122095743 blocks
6104787 blocks (5.00%) reserved for the super user
First data block=0
Maximum filesystem blocks=4294967296
3727 block groups
32768 blocks per group, 32768 fragments per group
8192 inodes per group
Superblock backups stored on blocks:
32768, 98304, 163840, 229376, 294912, 819200, 884736, 1605632, 2654208,
4096000, 7962624, 11239424, 20480000, 23887872, 71663616, 78675968,
102400000
Writing inode tables: done
Creating journal (32768 blocks): done
Writing superblocks and filesystem accounting information: done
This filesystem will be automatically checked every 35 mounts or
180 days, whichever comes first. Use tune2fs -c or -i to override.
marc@fozzie:~$ sudo cryptsetup luksClose backups01
And that’s it. At this point, I turn off the drive, wait a few seconds, and then turn it back on and Gnome automatically prompts me to unlock the volume:
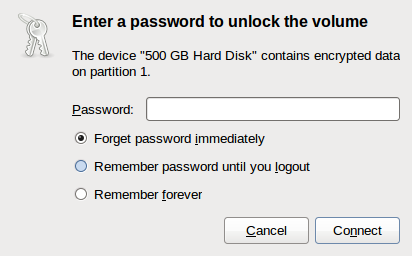
After entering the correct password, it will automatically mount using the volume label I specified, backups01, and appear in the file manager, ready to use. When finished using the volume, I use the Nautilus “eject” button to unmount the drive and its ready to be taken off-site.
There are many ways to set up encrypted volumes, this way is the best, easiest and most convenient for me.
I'd love to hear about what you've built or if you've got a topic you'd like me to post about.
This post is archived, comments are disabled.